This Week in Software Supply Chain Security: May 2 - May 8, 2024
Do you know what was in your cache last night?
Welcome to This Week in Supply Chain Security, your essential weekly resource for the latest developments in software supply chain security. Each week, we bring you critical insights and updates to help you stay ahead in safeguarding your software supply chain. Brought to you by the open source security experts at Stacklok.
🚨 Recent Security Incidents
A selection of the most impactful security breaches or threats in supply chains
Actions Cache Poisoning
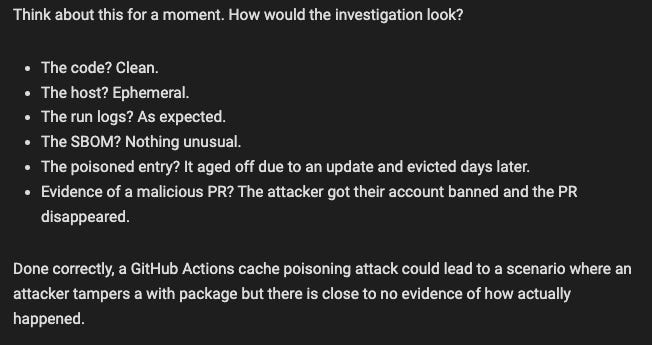
Continuing his theme of GitHub Actions supply chain attacks, Adnan Khan explained a number of attacks on the cache API for Actions. Successful targets included Angular, MDN, and Chainguard. His takeaway was: Never run untrusted code within the context of the main branch if any other workflows use GitHub Actions caching. By attacking the cache, Adnan was able to corrupt the output of workflows which used the caching feature, without affecting features like artifact attestation. He also highlights that a number of popular components, including setup-go enable caching by default, which may be unsafe in combination with pull request workflows which attackers could use to stuff poisoned entries in the cache. It will be interesting to see where this one goes.
GitLab CVE Writeup — Reflections on a Tricky Bug
GitLab wrote up their investigation of CVE-2024-0402, a vulnerability fixed in January. This vulnerability allowed an arbitrary file write on a GitLab instance, which could then allow for arbitrary command execution. The actual path to the vulnerability is kind of wild, including a mix of Ruby and Go code, as well as the devfile Gem and YAML parser differences.
Also, GitHub CVE Writeups
Since fair’s fair, there’s also a writeup of how a security researcher discovered CVE-2024-0200, a bug enabling remote execution on GitHub Enterprise servers, as well as disclosure of all environment variables including keys and secrets on github.com. Apparently the timing of discovery was really painful for GitHub (day after Christmas), but the underlying bug in Ruby sanitization may be interesting for all you Rubyists out there.
💡 Free Tools and Tips
New open-source and free (as in beer) supply chain security tools
Using GitHub Artifact Attestations
Stacklok (my employer) published a blog post about how to use GitHub’s new Artifact Attestations feature in Minder. Minder is Stacklok’s tool for securing open source repositories, and is free for public GitHub projects. The blog post describes how Minder is able to verify and apply policies based on artifact attestations and alert if artifacts are built by an unexpected workflow. Given that the GitHub feature was released a week ago, that’s a good turnaround on practical applications.
Bogus CVEs
GitHub user vin01 has created a list of bogus CVEs. As they point out in their README, anyone can request a CVE, without needing to get in touch with the software maintainers. It’s possible to dispute a CVE (and they include a guide), but that first requires the maintainers notice it. So now we know that CVEs may not indicate real security problems, and not all security problems have a CVE. We can also count those things really well…
👀 Community and Public Sector Updates
DruBOM: Another SBOM
OpenSSF announced a Drupal-specific SBOM called DruBOM. Given that there are already multiple SBOM formats, what makes DruBOM different than all the others? Apparently, it’s a Drupal module, so it integrates with the existing PHP Composer build stack, and then invokes Syft to generate a an SBOM in one of the existing formats. The creators recommend distributing the DruBOM alongside your release package. No word on signing and verification yet, but may be a thing to watch in the Drupal space.
That’s all for this week! See you next Thursday…